How The Recent White House Executive Oder Impacts Your Organization’s Cybersecurity

On May 12, 2021, The US President issued an “Executive Order on Improving the Nation’s Cybersecurity.” This announcement came soon after the Colonial Pipeline Cybersecurity Attack. The cyber-attack exposed weaknesses that exist in the federal cybersecurity infrastructure. Even after paying over 5 million dollars in ransom to recover the data, the pipeline’s temporary shutdown had […]
What is Behavioral Biometrics?

Security practices of the past and present are becoming increasingly ineffective in protecting data as attackers are getting more sophisticated. New technologies are now required to better protect your organization and your customers. Behavioral biometrics is a leading technology aimed at addressing these weaknesses. Traditional Biometric Authentication Traditional biometric authentication would include fingerprint readers and […]
If You’re Reading This, Change Your Password

Is your password still your dog’s name followed by an exclamation point? If so, it’s time to change your password. Far too many people, including employees handling your company’s data, are using weak passwords. The First Thursday of May is also known as World Password Day. In honor of World Password Day, here are some […]
Navigating IAM in the Cloud

75% of all cloud security breaches are a result of poor permission management according to Gartner. As your organization continues to work in the cloud, ensuring that you have the right identity access management tools are essential to best protect your organization. Identity access management (IAM) helps to grant access to the right assets for […]
Addressing Shadow IT

How many third-party Software as a Service (SaaS) applications do you use during the workday? Does your IT department know about all of them? This could introduce Shadow IT into your organization’s environment. The prevalence of Shadow IT has grown increasingly prevalent in the past year as more employees work from home and utilize SaaS […]
Meet Multiple Security Frameworks on One Platform
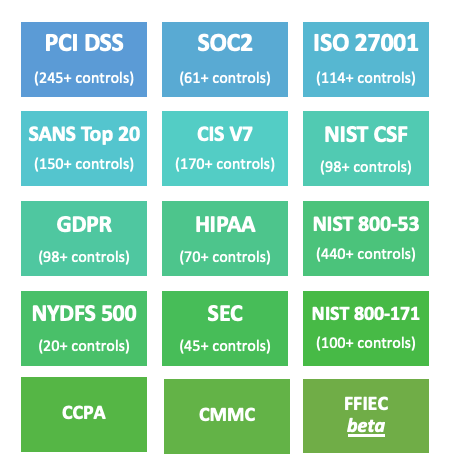
As your organization matures, you may need to meet additional security requirements. For example, many organizations that were previously required to comply with the NIST frameworks now must additionally comply with CMMC. Whatever compliance standards apply to your organization, Aurora can help you harmonize these existing frameworks and apply them to the additional frameworks. At […]
3 Key Aspects of Cloud Conformity

Platforms such as AWS and Azure provide a secure cloud infrastructure that is increasingly being adopted by leading organizations. When you adopt these platforms, you are responsible for protecting your own workloads, applications, and data—that is where Trend Micro comes in. Cloud Conformity helps to continuously secure your cloud infrastructure by enabling you to: 1. […]
Application Security: What You Need to Know

For Application Security to be effective, it must work fast. Trend Micro’s Cloud One Application Security automatically detects attacks and gives you the visibility to prevent the attack from happening again. There are numerous threats and vulnerabilities that may impact your apps. Cloud One Application Security helps you with prioritizing remediation and protection, and anti-malware […]
Cyber Threats to Look Out for This Valentine’s Day

You’ve heard that there are plenty of fish in the sea–but did you know about all the phishing that takes place every year in honor of Valentine’s Day? Any holiday that centers around online shopping sparks increased cyberattacks. Here are a few trends to look out for this Valentine’s Day: Phishing Emails: If you receive […]
SolarWinds Impact for Security Managers

The cybersecurity community continues to investigate recent attacks that are linked to SolarWinds. The popular network monitoring software, SolarWinds Orion, was compromised by a massive, sophisticated attack on December 13, 2020. The attackers planted a backdoor known as Sunburst onto affected machines, gaining complete access to the targeted organizations’ network. The recent SolarWinds attack raises […]

