How Failure of Cybersecurity Tools Are Impacting Business Operations

Introduction In the late forties when American aerospace engineer Edward Murphy suffered the mortification of witnessing a mishap in his rocket sled tests, he unwittingly popularized one of the best known of the Murphy Laws – If something can go wrong, it will. Though the ‘law’ was more in the manner of a humorous statement, […]
Defending Against Watering Hole Attacks in Today’s Cyber Landscape
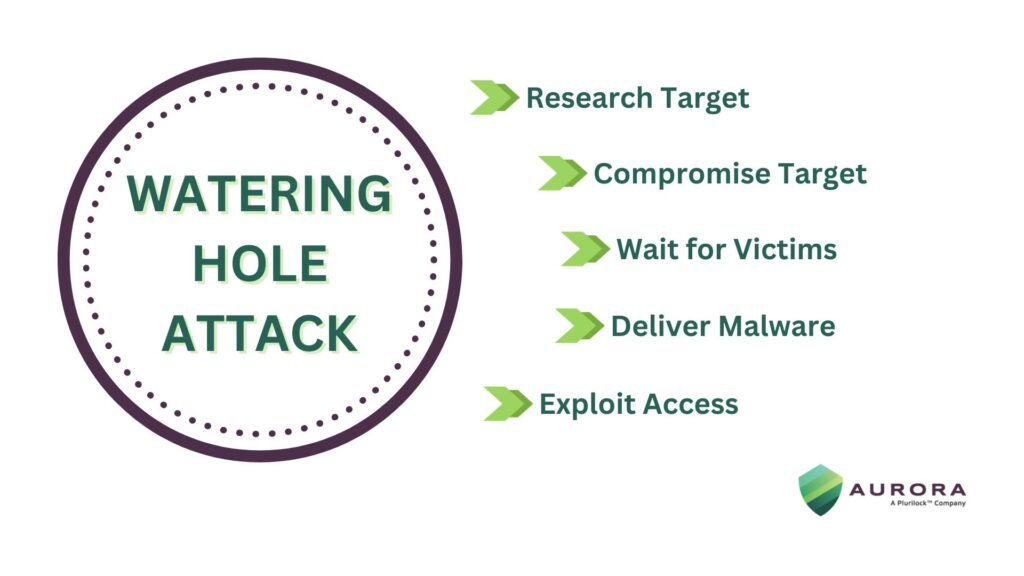
Introduction The Chernobyl disaster in 1986, one of the most catastrophic nuclear accidents in history, remains a powerful reminder of the devastating consequences of a targeted failure. The explosion and subsequent radiation release at the reactor were the result of a deadly combination of design flaws and human error, strategically exploited during a routine safety […]
Soft Skills Transforming Cybersecurity Professionals

Introduction From the way ‘soft skills’ has taken center stage in many professions, you’d think it is a concept that is only around a decade or so. Not so. The history of soft skills goes back to the late sixties/early seventies and is credited to the American armed forces (1). The then army strategists found […]
Securing Our Schools – Combatting the Surge in Cyberattacks on K12 Education

Introduction Though child abuse is an odious comparison, it can be argued that the increasing cyberattacks on K12 schools, students, and their hapless families are just as devastating. ‘Catch ‘em young’ seems to be a phrase that is being cruelly twisted out of context by hackers intent on monetizing their nefarious ends at the cost […]
The 5 W’s of Data Classification
There are several routes to Regulatory Compliance, but the journey has to include Data Classification. At the heart of becoming compliant, is an effective Data Security Strategy – which in the perfect world would keep our information assets safe from unauthorized access (aka Hackers and Data Thieves). Regardless of the compliance requirement: HIPAA, ITAR, EAR, PCI, […]
Cyber Insurance – Why Insuring Your IT Infrastructure is a Must
Target…Neiman Marcus….Home Depot….and now Chase, Cyber Breaches are now a mainstay of Corporate America and will be for a long time to come. Although the first few IT Security breaches had caused uproar in the media and panic within the general public, it seems that as of now, these breaches are commonplace and even expected […]
EAR Compliance and Data Classification Pt. II; Categorization
Equally important as classifying EAR Sensitive data, is categorizing it. Once data is deemed as sensitive or non-sensitive, an organization must apply a set of categories that will differentiate data based on confidentiality and authorization. While it’s understood that an inherent rule of EAR compliance demands that EAR Sensitive data not be seen by non-US […]
EAR Compliance and “Technical Data” Explained
Although EAR Compliance has been around for quite some time now, IT security has just begun to become a major tenant it’s requirements. One of the most important components to understand, in respect to EAR Compliance, is what exactly classifies as EAR regulated items or “Deemed Exports”. The definitions have always been a tad difficult […]
EAR Compliance and Data Classification
Export Administration Regulations (EAR) is a set of US Government regulations that deals with the export and temporary import of items designed for commercial use, which could have military application (Dual Use). The sensitive information in an EAR context is usually defined as “Technical Data” which includes; articles, technology, software, and other information necessary for […]
Data Security Best Practices for EAR Compliance
EAR Compliance is very similar to ITAR Compliance. However, while ITAR covers military items or defense related technical data, EAR Regulates items designed for commercial purpose which could have military applications such as computers or software (Dual Use). Logically, this includes technical data as well as other information stored on servers and hard drives. As […]

