Resources for Log4j Vulnerability

If you are not already aware, on December 9, 2021, a zero-day vulnerability on Apache Log4j, nicknamed “Log4Shell” was reported. It has been characterized as “the single biggest, and most critical vulnerability of the last decade.” Many people may have not heard of the Log4j software until the attack was first uncovered, however it is […]
EDR, XDR, and MDR: Improve Your Detection & Response

Going Beyond EDR You probably are already familiar with Endpoint Detection & Response (EDR). It is a valuable solution for detecting and responding to threats inside managed endpoints. This is a great way to minimize the threats of cyberattacks like malware and ransomware. EDR, however, can have its limitations. By only detecting and responding around […]
The ABCs of Cybersecurity

With the fear of being the next victim of a cybersecurity breach, organizations may be tempted to purchase any “next best thing” solution before first meeting basic cybersecurity requirements. Quieting out the noise, we are often reminded by peers in the cybersecurity industry to go “back to the basics.” While we endorse many security solutions […]
How to Implement Zero Trust?

Zero Trust is a cybersecurity framework that aims to eliminate trust from an organization’s network to help prevent attacks. Zero trust was first introduced in 1994, so you probably already know that its basic principle is to “never trust, always verify.” It is designed to protect organizations by segmenting networks, preventing lateral movements, simplifying access […]
The Launch of CMMC 2.0
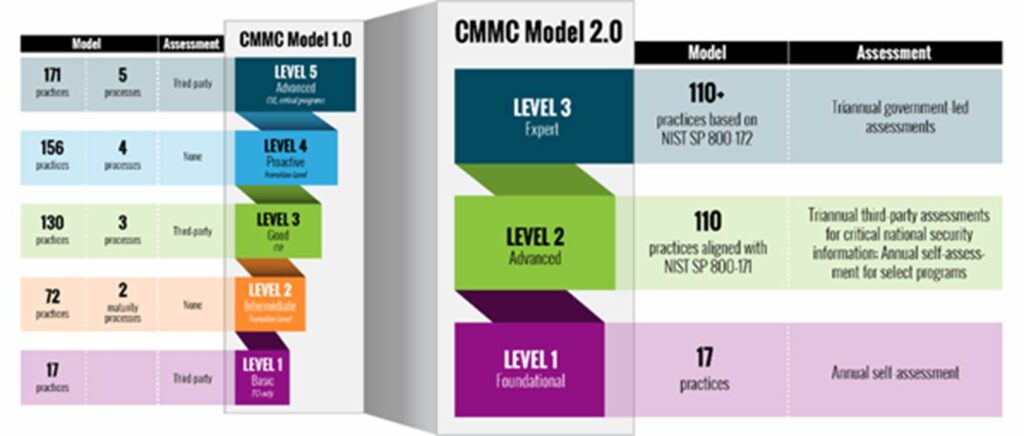
The Pentagon recently announced a new version of the Cybersecurity Maturity Model Certification (CMMC) requirements. CMMC 1.0 was announced in 2020 and CMMC 2.0 indicates an effort to strengthen the new security standard. One of the biggest changes in CMMC 2.0 is that it reduced the levels of security compliance from five to three. The […]
Honoring and Thanking Cybersecurity Teams

Holding cybersecurity as a focus of our business, it is important for us to appreciate all of the security teams that we work with to protect customer data. Whether it is Aurora’s internal security teams, our partners, or the customers that we work with, join us in celebrating them. Here are some of the many […]
Making Cybersecurity a Priority

Cybersecurity should be your first consideration when conducting business and navigating the web. As your business constantly adopts new technologies and policies to adapt to a fast-growing world, security should also be considered. Ask yourself if this new technology is protected by your existing cybersecurity tools and take the actions necessary if you are not […]
It’s Clean Your Virtual Desktop Day: Why You Should Celebrate

Every year on the third Monday in October, “Clean Your Virtual Desktop Day” is celebrated. Just like how our physical desktops need to be cleaned for finger smudges and food crumbs, our virtual desktop needs cleaning too. There are many benefits of cleaning your virtual desktop—one of them being improving your cybersecurity posture. Performance If […]
Red, Blue, and Purple Teaming – What’s the Difference
Many mature and sophisticated infosec teams are moving their focus from traditional penetration testing engagements to Red Teaming exercises. As you consider this move, what should you look for in a Red Team vendor? Capabilities and objectives can vary wildly. For starters, let’s look at the differences between red teaming and what’s known as purple […]
Where Do National Cybersecurity Improvements Begin?

Even organizations with cybersecurity measures in place are being affected by cyberattacks. Critical infrastructure, healthcare, and state & local government agencies have been frequent targets for attackers. An attack on any organization can impact far more than just customers and employees. As the cybersecurity community, how can we recommend improvements that can minimize the impact […]

